Getting a Windows XP workstation to join a domain with a Windows 2019 Server domain controller requires more than just enabling SMBv1, despite what most Google results on the topic would tell you. My former colleague and I had attempted to upgrade our DC a few years back from Windows 2012R2 to Windows 2019. In doing so, we found that all Windows XP SP3 workstations began to exclaim that their trust relationship with the domain had ended. Attempting to rejoin the domain resulted in a failure message of “An internal error occurred.”
It turns out, the XP machines also require Hotfix KB969442 and Security Patch to fix a problem XP has with AES.
The hotfix requirement was mentioned in passing on Reddit a few years ago. But I also found a reference to this KB in another blog post which itself references an even older blog post from 2011.
That original 2011 blogger to his credit provided specific Wireshark evidence showing how the original Windows XP kerberos.dll had a bug that prevented it from handshaking with the DC using AES. I presume that our Windows 2012R2 server (running at a 2012R2 functional level) permitted RC4 fallback in a manner that Windows 2019 does not.
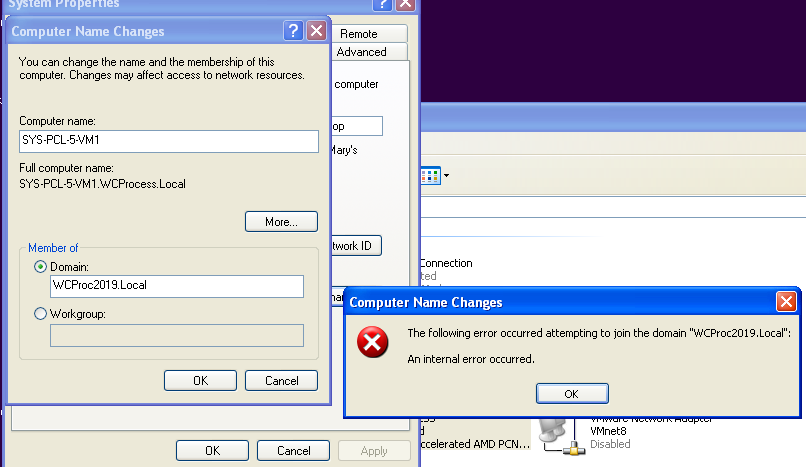
To test the efficacy of these changes, I started first with a Windows 2019 Standard Server edition with SMBv1 enabled. I promoted this server to a domain controller and attempted to join my WinXP SP3 VM to its domain. I got the internal error.
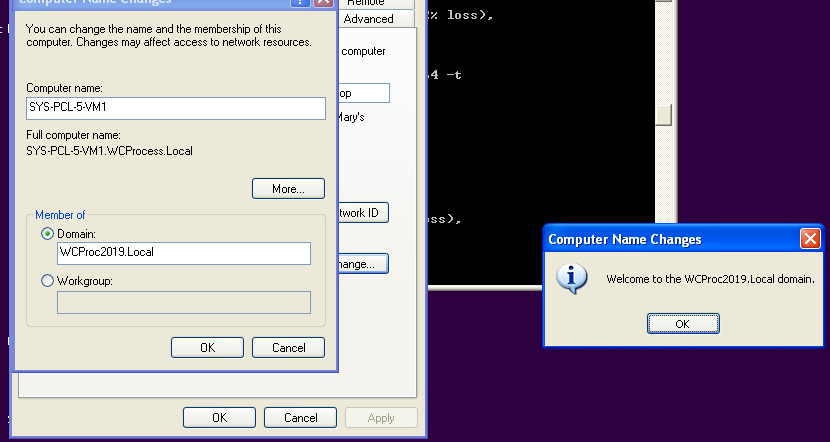
I then applied the Hotfix and tried again. Voila!
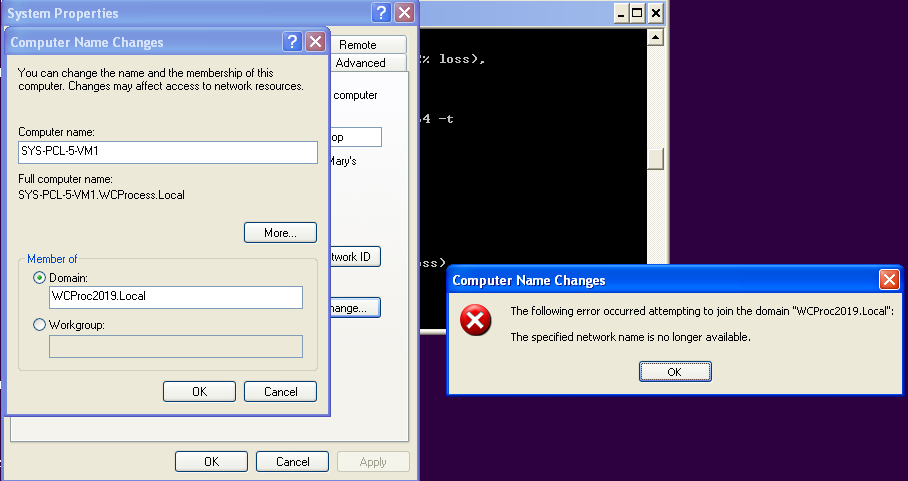
Lastly, to confirm that SMBv1 is required here, I disjoined the XP machine from the domain and disabled SMBv1 on the domain controller.
Set-SmbServerConfiguration -EnableSMB1Protocol $false
Interestingly, the error message that resulted was different this time. “The specified netowrk name is no longer available.”